How To Secure Business Endpoints & Identities
Exposed, unknown endpoints on business networks are more than a cyber security threat; they’re a brand liability.

Forrester’s Security and Risk Summit made a compelling case for how technology trust is key to driving brand trust.
They highlighted how enterprise’s effectiveness at improving their cyber security posture directly affects their profits.
Jeff Pollard, VP and principal analyst at Forrester said, “When something touches as much revenue as cybersecurity does, it is a core competency, and you can’t argue that it isn’t.”
Many CISOs face the challenge of consolidating tech stacks while supporting a growing base of endpoints and identities.
Zero-trust network access (ZTNA) and zero-trust edge are core to zero-trust frameworks. Zero trust does not have to be expensive to be effective.
Allie Mellen, a senior analyst at Forrester, noted that, “Zero trust goes hand in hand with trust. Because what you can do is make sure that all of your devices are secure and safe. And that even in a potential physical conflict, you must move your entire team out of the country. Suppose they leave a device behind.”
“You can manage that risk; you can wipe that device; you can make sure that nobody is going to get access to customer data on that device,”she said.
It’s incredibly importantfor every business to stay agile and adaptive to potential geopolitical risks.
Securing Anywhere-Work Endpoints
Paddy Harrington, senior analyst at Forrester, highlighted several insights that organizations could use to protect their endpoints.
CISOs and their teams need to adopt more effective mobile application management and endpoint management strategies to support how fluid anywhere-work scenarios are becoming.
Understanding if an endpoint is trusted, tracked and known has a significant impact on revenue.
On-premises endpoint protection platforms (EPP) don’t provide the visibility enterprises need to secure and keep endpoint configurations current.
That lack of visibility into endpoint health and status drains revenue.
The on-premises deployments of endpoint protection showed their flaws, and one of the biggest flaws in this was a loss of visibility of what’s going on at the endpoint.
Enterprises moving to web apps combined with record rates of bring your own device(BYOD) adoption made clear that on-premise EPP was not up to the new challenges enterprises are facing.
These Business Endpoint Security Challenges Include:
Increased XDR Demand & Endpoint SecuritySpending
Faced with the challenge of securing an increasingly mobile, fluid inventory of endpoints supporting anywhere-work scenarios, CISOs are making endpoint security a high priority in 2023.
- 26% are going to stay at current budget levels for endpoint detection response (EDR) and extended detection response (XDR).
- 62% will increase their spending on EDR and XDR in 2023.
- 88% of the security leaders we have researched said that they expect to maintain or increase their budgets in cyber security technology by 2022 to 2023.
Endpoint platform vendors continue to see growing interest in XDR with their largest enterprise customers.
VentureBeat interviewed several CrowdStrike enterprise customers at the company’s Fal.Con event held earlier this year who noted that XDR will help them consolidate their tech stacks in 2023, reducing costs and improving endpoint visibility.
Cloud-Native Endpoint Platforms
The cloud has won the battle for endpoint platforms by providing faster time to value, a shorter time to get users up and running, more flexibility in defining user experiences, automating patching, strong API support for integration, and self-healing.
When moving to the cloud, we want to look for cloud-native solutions built in the cloud, as opposed to taking an on-premises deployment and reengineering it for that anywhere delivery model.
Cloud-native solutions give you the greatest flexibility and the most options.
Forrester’s endpoint management report, from earlier this year, explains what CISOs need to look for in planning their endpoint strategies for 2023 and beyond.
The research underscores how prevalent cloud platforms are becoming, and how critical self-healing endpoints will need to occur at multiple levels including:
- Application
- Operating system (OS)
- Firmware
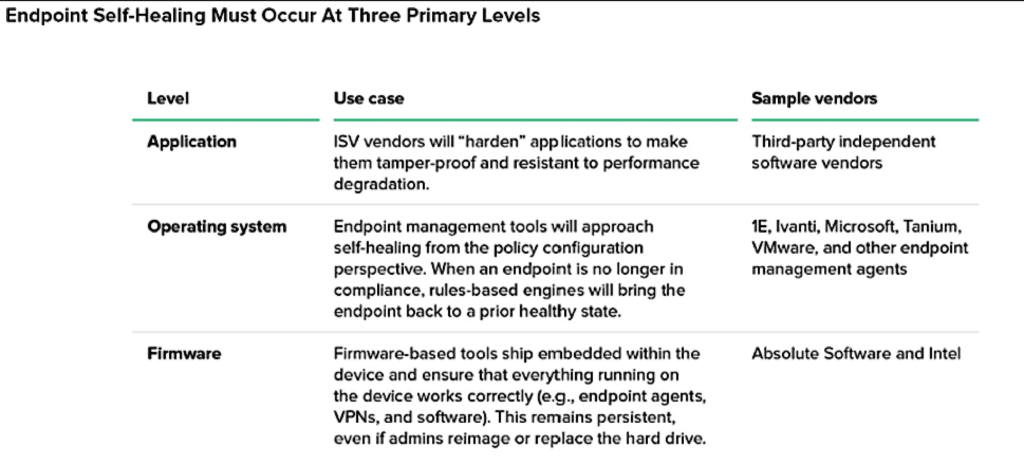
The report states that self-healing embedded in the firmware will prove the most essential because it will ensure that all the software running on an endpoint. Even agents that conduct self-healing at an OS level, can effectively run without disruption.
Firmware-level self-healing helps in several ways:
- It ensures that any corruption in the firmware is healed in and of itself.
- Ensures that agents running on the devices heal.
For example, suppose you have an endpoint security agent running on an endpoint and it crashes or becomes corrupted somehow.
In that case, firmware level self-healing can help to fix it quickly and get it properly functioning again.
Leading providers of cloud-based self-healing endpoints include Absolute Software, CrowdStrike, Ivanti, Microsoft, Tanium, VMWare and others.
Firmware-based self-healing endpoints create an undeletable digital tether to every PC-based endpoint.
Unified Endpoint Management (UEM) is key to security and asset management
This is key tp cyber security and asset management.
CISOs should also consider how unified endpoint management (UEM) leads to better endpoint security and asset management on the same platform.
Unified endpoint management (UEM); sometimes we forget that basic things like policy control and OS control should be considered part of security deployment.
They shouldn’t just be reserved to its configuration policies. They should be an integrated part of clearing the endpoint.
UEM is essential for ensuring every mobile device is secured to the application and browser level.
Advanced UEM platforms can also provide automated configuration management and ensure compliance with corporate standards to reduce the risk of a breach.
In addition, CISOs are exerting pressure on vendors to help consolidate tech stacks.
As a result, product strategies and roadmaps from IBM, Ivanti, ManageEngine, Matrix42, Microsoft, VMWare, Blackberry, Citrix and other vendors reflect CISOs’ needs for more consolidated cloud platforms capable of reducing the costs of their tech stacks.
Remote Browser Isolation (RBI)
This provides maximum control with minimum impact. One of the key points made during the session is how pervasive web applications are across enterprises today.
For example, 63% of information workers Forrester recently interviewed say that all their work can be accomplished using a web browser. Another 31% say most of their work can be done in a browser and local apps.
“What we want to do is look for the use cases that will provide us the maximum amount of control with a minimal impact on the users,” Harrington said.
“Some of the ones that do this are utilizing RBI for contract or with third-party actions so that you can do things like watermarking or clipboard control or download control and truly segment this application from the user.”
RBI has proven effective as a solution for organizations that rely on outside contractors and third-party access, who are also pursuing a ZTNA-based approach to protecting browser sessions.
IT and security teams are adopting RBI because it doesn’t force an overhaul of tech stacks while still providing a zero-trust security approach to browsing.
Leaders in RBI include Broadcom, Forcepoint, Ericom, Iboss, Lookout, NetSkope, Palo Alto Networks and Zscaler.
Of these, Ericom is taking a unique approach to zero-trust RBI by preserving native browser performance and user experience while hardening endpoints from increasingly complex web threats.
RBI is used across enterprises to secure Office 365, Salesforce and many other cloud-based app sessions and their data.
RBI protects these apps and browser sessions from potentially malicious unmanaged devices, including those used by contractors or partners.
What Works To Protect Anywhere-Work Endpoints
The cloud has won the endpoint platform market and is gaining fast in replacing installed, legacy endpoint protection platforms.
That is good news for CISOs under pressure to make budgets go further while consolidating their tech stacks and gaining visibility beyond their endpoints.
Unfortunately, the typical enterprise struggles to track all endpoints and have a complete view of every asset.
Forrester’s session on protecting anywhere-work endpoints provides new insights into how enterprises can improve endpoint security without disrupting employees’ productivity, while helping reduce the costs and tech stack complexities of building toward a zero-trust framework.









ivistroy.ru
July 17, 2023It’s really a nice and helpful piece of information. I’m glad that you shared this helpful info with us. Please stay us informed like this. Thanks for sharing. ivistroy.ru