Business Cyber Security: 8 Mistakes That Let Hackers In
Cyber security awareness: Unfortunately, small to medium sized businesses make very tempting targets for malicious hackers because they leave themselves vulnerable to cyber threats.
SMBs hold the same kinds of data that large businesses have, such as personal information, credit card details, passwords, and more.
However, with the nature of SMBs means the information could be held less securely than within a large organisation. Particularly, if there isn’t a CIO or Managed IT Service Provider to keep the business up, running, and protected.
Without the proper cyber defences or cyber security plans in place, you’re an irresistible target for cybercriminals, and your business won’t be able to defend itself against malicious campaigns.
SMBs are also a prime target for hackers because if they compromise a business that’s asupplier to a larger business, they can also gain access to that company, to carry out a larger supply chain attack.
No matter what kind of cyberattack a business falls victim to, whether that’s phishing, ransomware, malware or any other malicious activity where attackers access and tamper with data, the results can be devastating.
In some cases, the cost of falling victim to a cyberattack has even forced organisations to close permanently. Fortunately, it’s possible to help keep your business and employees more secure online.
Enhance your business cyber defences by avoiding these cyber security pitfalls:
1. Don’t Use Weak Passwords
Cyber criminals don’t need to be super-skilled to break into email accounts, cloud services and other applications.
In many cases, they get in because the account owner is using a weak or easy password.
Never base your passwords around easy-to-discover information, like your favourite sports team or pet’s name, because clues on your social media could give this away.
Cyber criminals commonly use brute-force attacks which quickly run through a list of commonly used or simple passwords.
The National Cyber Security Centre (NCSC) suggests using a password made up of three random words, like a passphrase to make it difficult to guess.
Many people use simple passwords across multiple accounts,because remembering many different passwords can be difficult, but this leaves businesses beyond vulnerable to cyberattacks.
A different password should be used on each account. A password manager can greatly help solve this issue by removing the need to remember every password.
2. Don’t Ignore Multi-Factor Authentication
Multi-factor authentication (MFA) provides an additional barrier to account security.
It requires the user toto confirm that it really is themattempting to log in, via SMS message, authenticator app, or a physical security key.
The extra layer protects you because even if a criminal has the correct password, they can’t use the account without the approved access.
It’s not impossible that even a strong password can end up in the wrong hands. Cyber criminals often trick users via phishing attacks, to steal login credentials.
If you get an unexpected alert sof an attempted log in, you should report it to your IT security team and reset the password immediately to avoid continued attempts.
MFA or 2FA, is among the most commonly issued cybersecurity advice, but many businesses still aren’t using it, and that needs to change.
3. Don’t Put Off Applying Security Patches And Updates
One of the most common techniques used to breach and move around networks is taking advantage of cybersecurity vulnerabilities in applications and software.
When these vulnerabilities are disclosed, vendors who make operating systems will usually release a security update to fix them.
Security patches will fix the flaw as long as the update is applied, thus protecting the system from attackers attempting to exploit it.
Unfortunately, many businesses are slow to roll out security patches and updates, leaving networks and systems vulnerable.
Sometimes, vulnerabilities can be left unpatched for years, putting the business and customers at risk from cyber incidents that could easily be prevented.
One of the key things SMBs can do to improve cybersecurity is have a strategy for applying critical security updates ASAP.
You can set up the network so that software updates are applied automatically, or they can be dealt with on a case-by-case basis.
It’s vital to recognise critical security updates and patch them, they’re often detailed by cybersecurity agencies like CISA.
4. Don’t Forget About Antivirus Software Or Firewalls
Antivirus software is there to help protect users and devices, from cyber threats including malware and ransomware.
To improve cybersecurity, install next generation antivirus software across all devices on the network.
Nowadays, antivirus software is often bundled for free within popular operating systems, but there’s also the option of installing from a dedicated vendor.
As with other software, you can’t just ignore antivirus software after installing it.
It’s important to prevent antivirus tools from becoming obsolete against evolving cyber threats, so patch and update it regularly.
Business firewalls are also a virtual structure to have in place.
Firewall solutions comprised of either hardware, software, or both, that can prevent the spread of your private data to hackers, scammers, and other cyber criminals.
5. Don’t Leave Employees Without Cyber Security Awareness Training
It’s vital for businesses to provide their employees with the proper tools and training around cyber security awareness.
All it takesis one person inadvertently making an error to provide malicious hackers with a way into the network.
For example, they could mistakenly click on a link in a phishing email and install malware on the network, or they could fall victim to a business email compromise scam, and transfer a large sum of money to someone claiming to be a business partner or even their boss.
Providing employees education on how to recognise phishing emails, suspicious links and other potential methods of attack is vital for helping to keep data, money, personnel and customers secure.
Employees should also know who they should report potential suspicious activity to, so suspected cybersecurity incidents can be prevented.
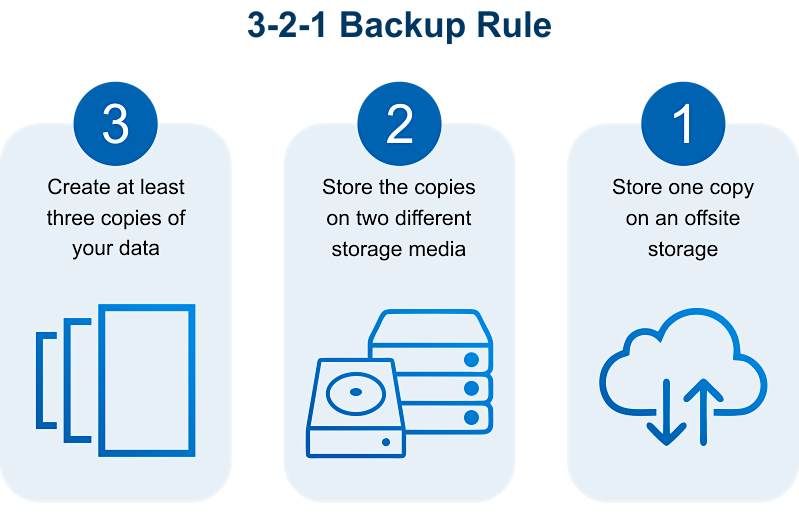
6. Don’t Ignore Backups & Recovery Plans
One of the key things you should be doing to make systems more resilient to cyberattacks is producing regular backups of your data.
Data is one of the most valuable assets your business has. Keeping that data protected and consistently available has become more critical than ever.
Every business needs a solid backup and recovery plan in order to survive and thrive in the face of an incident that encrypts, breaches, wipes, or brings down the network.
When backups are updated regularly, you’ll be ensured a recent copy of all your data can be restored, making for a relatively quick return to normal.
Today’s businesses are mixing and matching onsite and cloud-based backup strategies to create a system that works best for their specific goals.
7. Don’t Leave Your Network Unmonitored
Setting up the network with controls to help prevent cyberattacks is very useful.
This approach starts with knowing what internet-connected devices make up your network, because you can’t defend what you don’t know about.
These devices include computers, as well as, IoT devices, point-of-sale machines, security cameras, and potentially much more.
All these devices could be exploited by cyber criminals if they’re not managed correctly.
Taking the time to audit your network to fully understand what’s on it andensuring they’re protected with the right updates is vital.
Be aware of what’s regular behaviour and what could count as suspicious.
For example, if your suddenly seeing logins from the other side of the world, that could be a sign that something needs investigating.
8. Don’t End Up Facing A Cybersecurity Incident Without A Plan
Even if you have a solid cybersecurity strategy, there’s still a chance that cyber criminals could breach the network.
Whether that’s installing ransomware, conducting espionage, stealing credit card information or focusing on other malicious attacks.
In the event of an attack happening, it’s helpful to have a plan in place that’s accessible even if the network ends up offline.
Have a plan around how your business will respond to a cyberattack, how it could continue operating, and which cybersecurity agencies and investigators should be contacted.
This will help your business deal with a stressful situation with more structure of strategy and calmness.








