Sophisticated Phishing Targets LastPass Users: A Deceptive Chameleon Outsmarts Even the Savviest
The campaign deployed email, SMS, and voice calls to deceive targets into revealing their master passwords.
Company officials reported that LastPass users, utilizing a password-manager service, were recently targeted by a sophisticated phishing campaign. This campaign utilized a mix of email, SMS, and voice calls to deceive users into disclosing their master passwords.
The attackers employed a highly advanced phishing-as-a-service kit, uncovered in February by researchers from Lookout, a mobile security firm. Known as CryptoChameleon due to its emphasis on targeting cryptocurrency accounts, this kit offers a comprehensive suite of tools designed to deceive even tech-savvy individuals. It includes premium-quality URLs, a replica single sign-on page tailored to the victim’s service, and the capability to conduct real-time voice calls, emails, or texts while the target is on a fraudulent website. This end-to-end service can bypass multi-factor authentication measures if the target has it enabled.
Targeting LastPass
Lookout revealed that LastPass was just one among numerous sensitive services or sites targeted by CryptoChameleon. The list of victims also included the Federal Communications Commission, cryptocurrency exchanges like Coinbase, as well as email, password management, and single sign-on services such as Okta, iCloud, and Outlook. Upon accessing a database utilized by a CryptoChameleon subscriber, Lookout researchers discovered a substantial amount of collected data from the scams, including seemingly authentic email addresses, passwords, one-time-password tokens, password reset URLs, and even images of driver’s licenses. Typically, databases of this nature are filled with junk entries.
LastPass officials announced on Thursday that threat actors had recently utilized CryptoChameleon to target users of the password manager. They outlined the tactics employed in the campaign as follows:
- The scenario unfolds with the customer receiving a call from an 888 number, informing them of unauthorized access to their LastPass account from a new device. The caller then instructs the individual to press “1” to grant access or “2” to block it.
- If the recipient opts to press “2,” they are informed that they will shortly receive a call from a customer representative to “close the ticket.”
- Following this, the recipient receives a second call from a spoofed phone number, with the caller identifying themselves as a LastPass employee. Typically, this individual speaks with an American accent. They then inform the recipient that they will receive an email containing instructions to reset access to their account. However, the email sent is a phishing attempt, containing a shortened URL that directs them to the malicious “help-lastpass[.]com” site, aimed at stealing the user’s credentials.
- Should the recipient input their master password into the phishing site, the threat actor proceeds to log in to the LastPass account and alters settings within it to lock out the authentic user and seize control. These modifications could entail changing the primary phone number and email address, along with the master password itself.
The campaign specifically targeted LastPass customers on April 15 and 16, as confirmed by a company representative via email. LastPass successfully took down the fraudulent site on April 16.
This latest campaign marks another instance of LastPass being targeted. In August of 2022, LastPass disclosed its involvement as one of approximately a dozen targets in a series of attacks orchestrated by a single resourceful threat actor. Subsequently, in December, LastPass reported that the breach resulted in the theft of various data, including user password vaults and the cryptographically hashed passwords protecting them. Earlier last year, LastPass also revealed a successful breach involving an employee’s home computer, which contained a corporate vault.
LastPass has remained a target this year. An imitation app posing as LastPass was removed from the App Store. Additionally, LastPass reported last week that one of its employees fell victim to a deepfake audio call impersonating the voice of CEO Karim Toubba.
Seemingly Authentic?
Additional advanced features provided by CryptoChameleon include a captcha page, a unique feature designed to prevent automated analysis tools utilized by researchers and law enforcement from scanning the internet and uncovering phishing sites. This captcha functionality not only serves as a barrier to detection but also enhances the credibility of the page for targets.
Another capability offered is an administrative console that operators can utilize in real time to oversee visits to a spoofed site. Should a target input credentials, the operator can choose from a range of options on how to proceed.
According to Lookout researchers, attackers likely attempt to log in using the stolen credentials in real-time and then redirect the victim to a page tailored to the specific requirements of the multi-factor authentication (MFA) service being targeted. This could involve redirecting the victim to a page requesting an MFA token from their authenticator app or one prompting for an SMS-based token.
Attackers can engage targets via voice calls. Lookout observed instances where threat actors verbally guided targets through the steps necessary to compromise their accounts. Targets who spoke with Lookout researchers described the voices as having an “American” accent, being “well-spoken,” and displaying “professional call-center skills.”
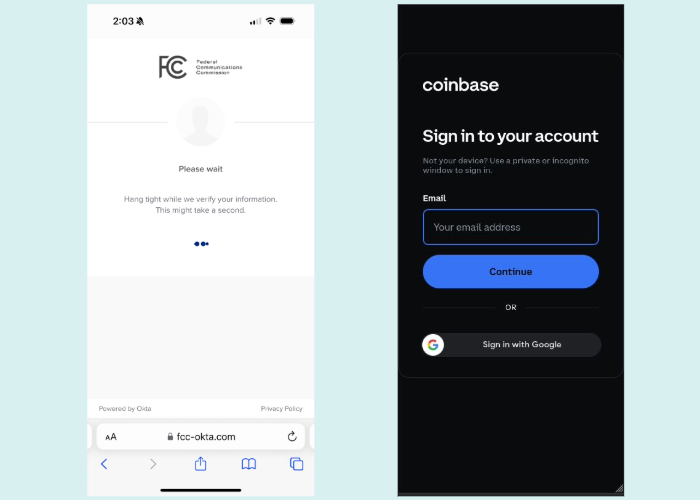
Based on the logs discovered by Lookout, the bulk of the login data collected originated from iOS and Android devices, suggesting that the attacks are predominantly focused on mobile devices. The majority of the victims were situated in the United States.
To prevent such scams, individuals should remember that incoming phone calls can be easily spoofed to appear to come from anywhere. Therefore, when receiving a call or SMS claiming to be from a service, recipients should promptly end the call and reach out to the service directly using its official email address, website, or phone number.
In a broader sense, both companies and end users should consistently implement multi-factor authentication (MFA) to bolster account security whenever feasible, ensuring it aligns with the FIDO standard when accessible. While MFA options such as push notifications or one-time passwords delivered via text, email, or authenticator apps offer some level of protection, recent events have underscored their vulnerability to credential phishing attacks.








