How To Build Your Businesses Cyber Security Resilience
Discover how organizations can build a culture of cyber resilience by reducing risk, limiting damage, having a disaster recovery plan and assuming a cyber attack is coming.

As a growing business, your ever-expanding digital footprint gives cyber criminals even more opportunity to extort money, disrupt your productivity, and generally wreak havoc for you and your teams.
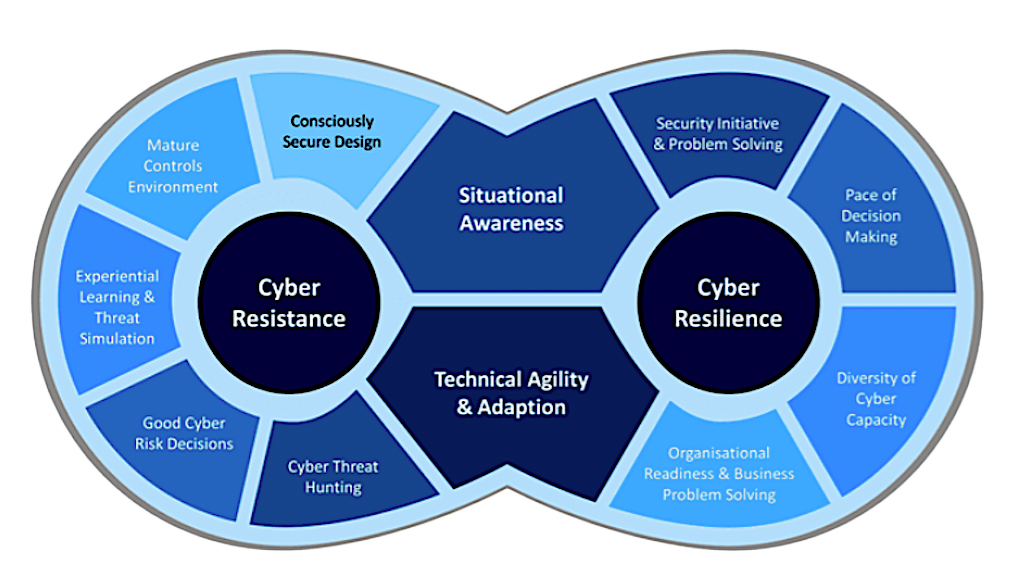
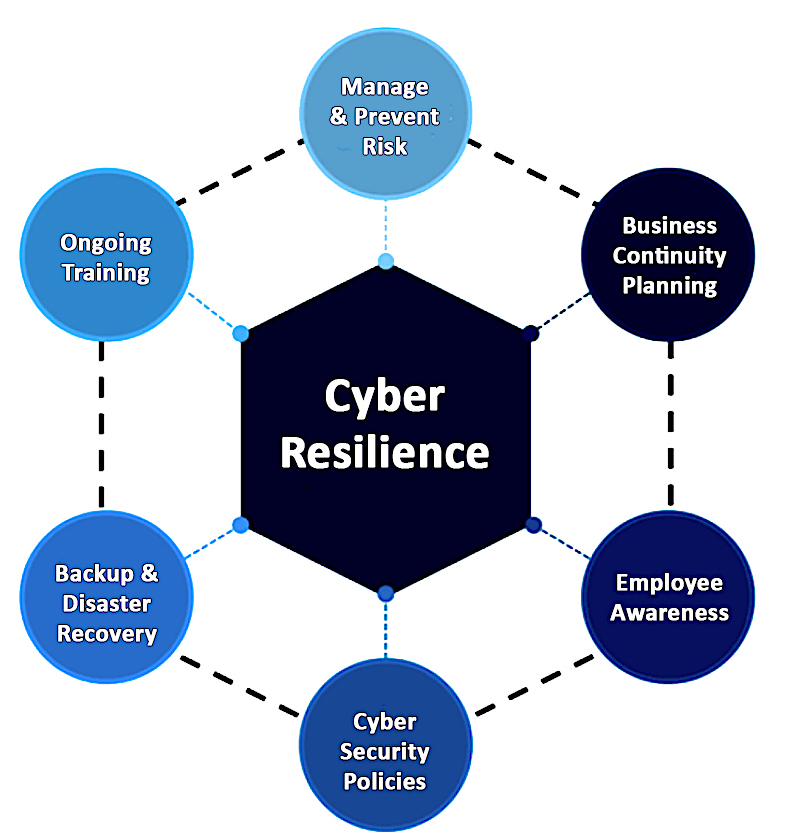
Cyber security and cyber resilience are not the same. They’re related, of course, but both have different demands, principles and mindsets.
Cyber security is an organization’s ability to protect its information assets from digital threats and vulnerabilities, whereas cyber resilience refers to an organization’s proactivity in being able to do the following:
- Anticipate where threats are going to come from
- Manage the attacks when they happen
- Have the visibility to adapt to future threats
Cyber resilience also assumes a breach has or will happen and provides the foundation to prepare and manage through a potential attack.
The attack surface that organizations need to defend is increasingly complex, and the threat landscape continues to rapidly expand.The reality is that an attacker only has to find one weakness or vulnerability.
Who Are We Up Against When It Comes To Cyber Security?
It’s important for business leaders to understand who and what they are up against when it comes to cyber crime. Know how to spot common tactics is key to protecting against them.
1. Ransomware Attacks
Small-medium-sized businesses are constantly getting hammered by attacks.82% of ransomware attacks are against companies with fewer than 1,000 employees.
Ransomware, a piece of malware can enter your system via an email or infected website. Once it has access to your local computer, it will attempt to penetrate the workplace network and steal valuable data.
Then, it begins to encrypt and lock you out of critical business systems until a ransom is paid. The threat of data leaks and reputational damage are common consequences of this type of attack.
Ransomware-as-a-service is a cybercrime business model between ransomware operators and affiliates in which affiliates pay to launch ransomware attacks developed by operators. This economic model unfortunately allows malware developers to earn money for their creations.
Many of these attacks originate on the dark web, where cyber criminals develop different attack methods and place them for sale. All of those pieces on the dark web marketplace can be automated to hit tens of thousands of businesses by just writing a script.
2. Multi-Factor Authentication (MFA) Fatigue
Multi-factor authentication (MFA) fatigue is also becoming an issue. MFA is a great piece of security, but applications that provide that type of security are now trying to make it more convenient.
However, convenience can be the enemy of security. Instead of requiring you to type in an MFA passcode, your phone may simply ask, ‘do you allow this login?’.
Cyber criminals are increasingly spamming users with these notifications until access is granted.
It’s important to note that the most common victims targeted in workforces were those that weren’t using multi-factor authentication (MFA) to secure their accounts.
3.Business Email Compromise (BEC)
Business email compromise is another widespread attack method and one of the most lucrative forms of cyber crime: According to the FBI, the combined total lost is over $43 billion and counting, with attacks in at least 177 countries.
By sending misleading emails that look like they come from the CEO or a vendor requiring payment, threat actors can persuade employees to share sensitive credentials or pay a fake invoice.
If the victim falls for it, the entire business could be left to deal with catastrophic consequences. Keeping up with the latest developments in email security is critical for your cyber defences.
How To Defend Against Cyber Attacks
Without the proper cyber defences or cyber security plans in place, you’re an irresistible target for cybercriminals, and your business won’t be able to defend itself against malicious campaigns.
As the technology world evolves rapidly, cyber threats to businesses are rising. A cyberattack couldhave a catastrophic impact on operations, resulting in costly disruptions, which makes reducing cyber risk an increasingly important business imperative.
Follow the steps below to fight back against hackers to avoid becoming their next victim.
10 Ways To Prevent Cyber Attacks:
- Staff Cyber Security Awareness Training
- Keep Software and Systems Fully Up To Date
- Ensure Endpoint Protection
- Install Firewalls and Next-Gen Antivirus Software
- Backup Your Data
- Control System Access
- Wifi Security
- Account Security
- Device Access Management
- Strong Passwords
Identify Cybersecurity Risks
Organizations need to be able to identify the risks and understand their risk surface. To effectively prioritize mitigation efforts, you must visualize the attack surface in context of the business services that make up the company.
Cybersecurity risk is simply defined as an effect of uncertainty on or within an information and technology environment. This can result in in the loss of confidentiality, availability and integrity for systems, devices, data, people and processes.
Reducing risk is a function of understanding the entire attack surface, understanding the business context of a compromise (for example, is it part of an application critical to the business or have a relationship with a critical application?)
Hybrid and multi-cloud environments, combined with containers, internet-of-things (IoT) technologies, SaaS applications, and digital supply chain concerns make this effort more challenging.
Here at BVA Technology Services, we help organizations of all sizes and industries take the necessary steps needed to identify and address gaps in their defenses.
It comes down to knowing what tools and services you have. Obviously you’re using computers, but are staff also using personal cell phones to access your company network? There’s a big risk there.
We ask questions like; How are you using your tools? Are you still using an email server down the hallway? Are you using Office 365?Where and how are your security investments are allocated?
While those can be the right solutions in the right place, communicating that to your provider is key. Who is using these tools? If you have teams that need remote access, things like this are critical for your IT provider to be aware of.
BVA uses our guidance and years of expertise to implement sound, best practice cyber security operations, technology, and infrastructure tailored to meet specific business needs and goals.
Cybersecurity Incident Response Plan
Planning for recovery involves working with your provider to determine what will happen if you are compromised.
This starts with two critical questions:
- Recovery Point Objective (RPO): How many hours can you afford to lose before it negatively impacts your clients, employees, or bottom line? How much rework are you willing to do? Is it a day, an hour?
- Recovery Time Objective (RTO): How long can you endure a system outage before it negatively impacts your clients, employees, or bottom line? How long can you go without your tools? This isn’t about rework, this is about having access to your systems in real time. For example, can you go a day without internet or email access?
If you can answer these questions, your provider can put together the appropriate tools and solutions for your specific business needs and goals.
Once you have structured these goals, you can hand the baton off to BVA, our technical ninjas will work through the other three aspects of your cybersecurity framework: protecting, detecting, and responding.
You can count on us to deploy the right tools, monitor your environment, carry out maintenance, and keep up with the future of technology in order to drive you towards success.
There’s a lot of work that goes into this, but no need to fear BVA is here!