New DDoS Attacks Are Sneakier & Harder To Protect Against
Cyber crime is on the rise, and cyber criminals are exploring new ways of conducting distributed denial of service (DDoS) attacks. Making them harder to protect against and more effective at causing disruption.
DDoS attacks are a relatively simple, but potent, form of cyberattack in which cyber criminals overload services with web traffic, slowing them down or taking them offline entirely, preventing others from being able to use them.
The attacks can range from short campaigns that last a few minutes to attacks strung out over extended periods of time.
These attacks often rely on malware-infected computers, servers and Internet of Things devices being connected into a botnet, which then overwhelms the target of the DDoS with web traffic.
While DDoS attacks are unsophisticated compared to other malicious cyber campaigns, they can cause significant disruption.
Large DDoS campaigns have temporarily severely disrupted online services, businesses and even the online infrastructures of entire countries.
The criminals behind DDoS attacks – who often lease out their services for others to use – continue to find new ways to make attacks more effective.
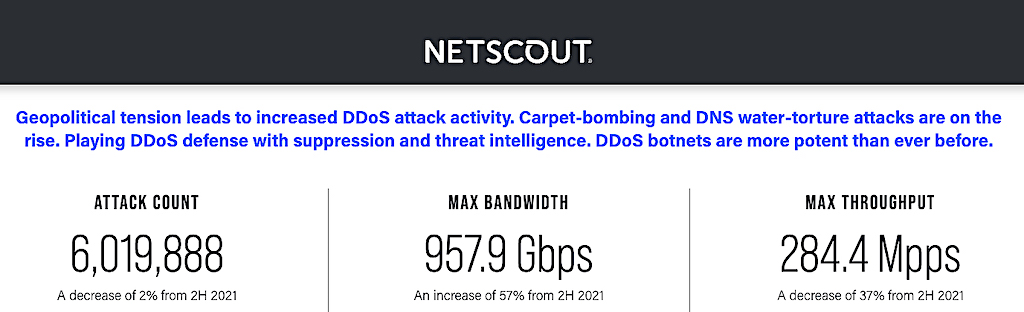
According to cyber security researchers at Netscout, who estimate that there were over six million DDoS attacks around the world during the first half of 2022.
That level of DDoS attacks is consistent with the previous six-month period, but as content delivery networks and cyber security providers get better at preventing DDoS attacks, attackers are finding new and innovative ways to power their attacks.
Researchers detail two methods of DDoS attack that have increased this past year:
First New DDoS Attack Type:
A wide range of services and/or devices are targeted with smaller portions of traffic compared to a regular DDoS incident.
The idea is that multiple different pipelines of the target are overwhelmed, without triggering the thresholds that would initiate protection against unusually high levels of traffic.
Many DDoS mitigation systems focus on individual IP addresses as opposed to entire subnets, so these attacks often fly under the radar.
Second New DDoS Attack Type:
Attackers send a huge amount of bogus subdomain requests in an attempt to overwhelm application-layer services.
“By constantly innovating and adapting, attackers are designing new, more effective DDoS attack vectors or doubling down on existing effective methodologies,” said Richard Hummel, threat intelligence lead at Netscout.
It isn’t just DDoS attacks that are evolving: cyber criminals are also putting resources into growing and adding features to botnets.
What are botnets?
A botnet refers to a group of computers which have been infected by malware and have come under the control of a malicious actor, and each infected device is called a bot.
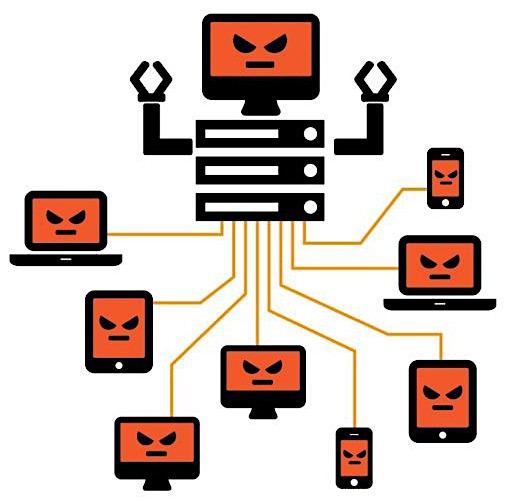
Botnets can be designed to accomplish illegal or malicious tasks including sending spam, stealing data, ransomware, fraudulently clicking on ads, and of course, distributed denial-of-service (DDoS) attacks.
By secretly infecting more machines with malware, cyber criminals can exploit them to launch larger attacks. The Netscout report suggests that botnets are getting bigger, both in terms of size and capabilities.
Botnets continue to evolve at a frightening pace, their capabilities expand with each passing year, and their targets now range from gamers to geopolitical enemies, researchers warned.
As threats of DDoS attacks continue to increase, it’s imperative forenterprises of all sizes to defend against these attacks or risk massive disruptions to service and reputation.
There are several steps organisations can take to amp up their DDoS attack protection and mitigation techniques.
These steps include using cloud-based hosting providers, deploying IP stresser services to test bandwidth capabilities, and employing a DDoS mitigation service.
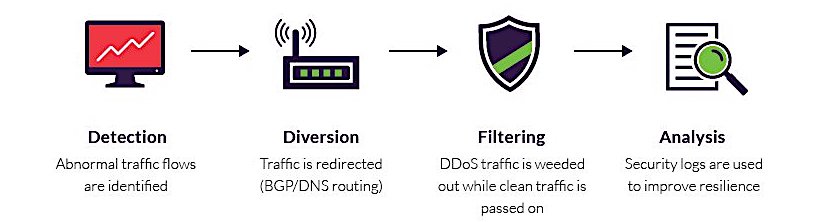
The Mitigation Process Stages
A typical mitigation process can be broadly defined by these four stages:
- Detection: The identification of traffic flow deviations that may signal the buildup of a DDoS assault. Effectiveness is measured by your ability to recognize an attack as early as possible, with instantaneous detection being the ultimate goal.
- Diversion: Traffic is rerouted away from its target, either to be filtered or completely discarded.
- Filtering: DDoS traffic is weeded out, usually by identifying patterns that instantly distinguish between legitimate traffic (i.e., humans, API calls and search engine bots) and malicious visitors. Responsiveness is a function of your being able to block an attack without interfering with your users’ experience. The aim is for your solution to be completely transparent to site visitors.
- Analysis: Security logs are reviewed to gather information about the attack, both to identify the offender(s) and to improve future resilience. The process’s effectiveness relies on the existence of detailed security logs that can offer granular visibility into the attack traffic.









Caiden H. F. Rowe
February 29, 2024Keep up the amazing work!
ufabet911
April 8, 2024You’re so awesome! I don’t believe I have read a single thing like that before. So great to find someone with some original thoughts on this topic. Really.. thank you for starting this up. This website is something that is needed on the internet, someone with a little originality!
ufabet911
April 9, 2024Very well presented. Every quote was awesome and thanks for sharing the content. Keep sharing and keep motivating others.