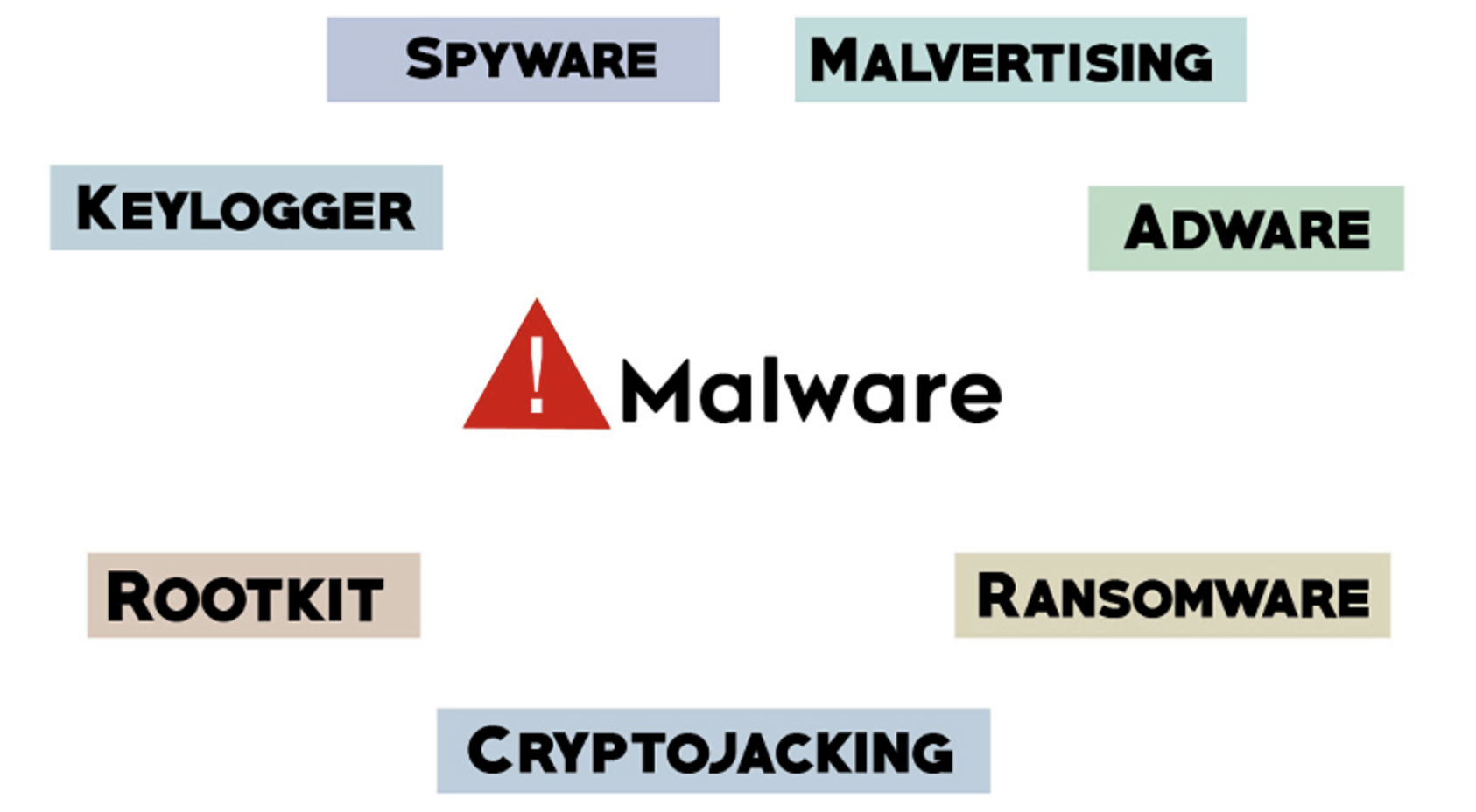
Learn how to boost your mobile security and protect your digital identity. This tech blog will run through different forms of malicious software on your iOS or Android handset, the warning signs of a spyware infection, and how to remove such pestilence from your mobile devices if it is possible to do so. The emails […]
Malware Cyber Security Awareness: Managed Threat Protection Malware is a broad term for any type of malicious software designed to damage or exploit a device, service or network. Cyber criminals use malware to gain remote control over victims’ devices, spy on user activities, steal sensitive data they can leverage for financial gain, or use the […]
Keeping on top of cybersecurity risks is a constant challenge. Threats including phishing, malware and ransomware are continually evolving and adapting, as cyber criminals regularly find new, innovative ways to conduct malicious hacking campaigns, break into computer systems and find a way to stay there. Many companies are having difficulties keeping up with the technological world and threats that come with […]
If you suspect you’ve been hit with a ransomware attack, it’s important to act quickly. Fortunately, there are several steps you can take to give you the best possible chance of minimizing damage and quickly returning to business as usual. 9 Steps For Responding To A Ransomware Attack 1. Isolate The Infected Device: Ransomware that […]
No one is safe from ransomware, and the attack methods are only getting more sophisticated. Ransomware is a type of malware that employs encryption to hold a victim’s information at ransom. Ransomware attacks are the most significant cyber security threat businesses face today. Many businesses are leaving themselves vulnerable because they don’t have an incident response […]
What is a DDoS attack? A distributed denial-of-service attack (DDoS attack) sees an attacker flooding the network or servers of the victim with a wave of internet traffic so big that their infrastructure is overwhelmed by the number of requests for access, slowing down services or taking them fully offline and preventing legitimate users from […]
Cyber Security Awareness: What Are Phishing Attacks? Phishing attacks are the practice of malicious actors sending fraudulent communications that appear to come from a legitimate trusted source. At its core, phishing is an attack methodology that uses social engineering tactics to make a person take an action that is against their best interests. The goal […]
Ransomware is the most significant cybersecurity threat facing many organizations today and while attacks are only getting more sophisticated, it’s a threat that can be countered. Several cybersecurity threats are facing the world today, including supply chain attacks, threat of cyber espionage and cyber aggression by hostile nation states, and cybersecurity exploits and vulnerabilities being sold to whoever wants to buy them. However, ransomware is the most immediate danger […]
Malware typically refers to malicious software comprised of worms, viruses, Trojans, and several other harmful programs. Hackers and spammers use Malware to damage your data and gain access to your confidential and sensitive information. While no device is immune to malicious software or infections there are effective security practices you can implement to help prevent […]