Defending Your Cloud Infrastructure From The Top Five Cybersecurity Threats
Cybersecurity threats continue to plague cloud infrastructures, and unfortunately, these threats remain unchanged from previous years.
Despite the persistent nature of these threats, it’s important to recognize that cloud security, when viewed holistically, can be just as robust as on-premises equipment. The long-standing debate, spanning over a decade, should finally be put to rest. Many information technology managers have gained two crucial insights: firstly, that data center technology doesn’t age well and accumulates significant technical debt, and secondly, the implied cost of future reworking required when addressing problems or outdated approaches over time.
Consider the example of Southwire Co. LLC, a company specializing in electrical cabling – the type of cabling utilized in hyperscale cloud facilities. Despite being over 70 years old, Southwire has migrated the majority of its infrastructure to Google Cloud, with this proportion steadily growing.
In this analysis, we outline five broad categories, describe some of the more notable exploits of the recent past, and offer recommendations for mitigating future risks. To compile this data, we used several reports, including Wiz Inc.’s State of the Cloud report for 2023, which analyzed over 200,000 cloud customer accounts, the Cloud Security Alliance’s survey on Top Threats to Cloud Computing, conducted among 700 industry experts in June 2022, and Palo Alto Networks’ Unit42 Cloud Threat Report using data from tens of thousands of sensors across their customers’ networks in April 2023.
Here’s what organizations looking to protect their cloud infrastructure should consider:
Securing cloud APIs and preventing data leaks prove to be more challenging.
Cloud providers continually introduce new services, accompanied by a plethora of new application programming interfaces (APIs) for interconnection. For instance, as per the Wiz report, Amazon Web Services Inc. has consistently introduced APIs, averaging around 40 new services and 1,600 new actions annually over the past six years. Additionally, the CSA report highlights the necessity of scrutinizing APIs and microservices for vulnerabilities stemming from misconfigurations, poor coding practices, insufficient authentication, and inappropriate authorization.
Alternatively, managing the utilization of APIs by applications, ensuring their proper configuration, and ultimately securing them poses significant challenges, as illustrated by Peloton’s experience a few years ago. The fitness company encountered a breach when its vulnerable API exposed sensitive customer data. Despite conducting scans for potential vulnerabilities, Peloton opted to disregard the recommendations of the security firm that discovered them.
“Leaked credentials are a common thread in every cloud breach we’ve analyzed,” noted Unit 42’s report. Identifying and removing hard-coded access credentials becomes increasingly challenging when faced with numerous cloud services and thousands of virtual machine instances to examine.
Why do these hard-coded credentials still exist? Primarily due to lax DevOps practices, such as granting full access rights across enterprise source code repositories. According to Unit 42’s report, over 80% of their customers utilized hard-coded credentials in their source control management tools.
The Fix
An effective approach to eradicate hard-coded credentials involves runtime code scanning. Numerous secret management tools, like HashiCorp Vault and Cloudflare Inc.’s Secrets Store, offer viable solutions. “For developers to maintain high velocity and for security administrators to feel confident, organizations must embrace a dependable and secure secrets manager,” said Cloudflare Inc. product manager Dina Kozlov. That is a good first step.
Also, Trail of Bits offers a new service called trusted publishing, which aids in authenticating code posted to open-source repositories using more reliable credentials. “Trusted publishing eliminates the need for long-lived API tokens and passwords, reducing the risk of supply chain attacks and credential leaks while streamlining release workflows. Critical packages on PyPI are already using trusted publishing to make their release processes more secure,” as stated in its announcement.
Additionally, In its latest threat report, Netskope Inc. provides a series of recommendations aimed at mitigating such leaks. These include enhanced inspection of downloaded files to thwart malware intrusions and blocking downloads entirely from untrusted or unused apps, newly minted domains, and risky file types.
SQL injection and cross-site scripting attacks persist
Despite being written over 20 years ago, one of my first stories highlighted the dangers of SQL injection, demonstrating how easily anyone could exploit it with a simple Google search. Unfortunately, little has changed since then. According to Unit42’s report, SQL injection and cross-site scripting vulnerabilities persist, consistently ranking among the top three most disclosed types of vulnerabilities.
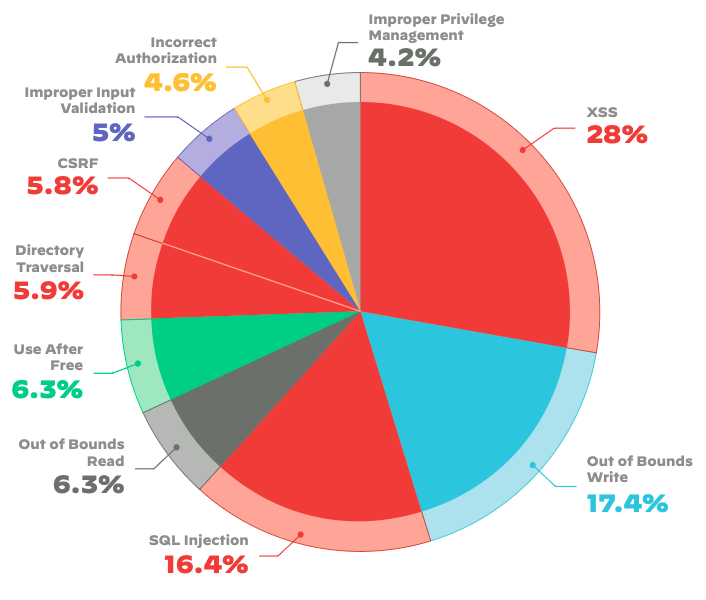
As shown in the pie chart, illustrates the total number of disclosed vulnerabilities from the previous year, with the red slices indicating those specifically relevant to web or API applications. The report points out the persistent growth of these exploits and references the ongoing web-based attacks on SolarWinds, which remain infamous. The authors note that even a year after the initial disclosure, there continues to be an escalating trend of exploitation attempts.
The Fix
Addressing these exploits may seem straightforward in theory. Netskope outlines several recommendations, including implementing improved input screening, gaining a comprehensive understanding of your application infrastructure, monitoring and firewalling network egress traffic, and using better DNS security to block potentially malicious domains. However, these basic tactics are notoriously difficult to deploy universally, as the number of SQLi and XSS exploits demonstrate.
Cloud breaches demand distinct tools and methodologies compared to on-premises
Securing a cloud environment requires different tools and techniques than securing on-premises systems. Unit42’s report highlights that traditional digital forensics and incident response techniques are ill-suited for addressing cloud breaches due to significant differences in tooling, processes, and data sources between on-premises and cloud environments.
The report cites the average time to resolve a security alert across all its customers as approximately six days, with half of them taking more than four days. “This presents a significant window of opportunity for potential adversaries to exploit newly discovered vulnerabilities,” the authors noted.
But even six days is a conservative estimate. Take, for example, a recent announcement from Toyota revealing that data from over 2 million customers had been accessible online for more than 10 years due to a misconfigured cloud storage bucket. Barracuda Networks Inc. experienced its breach last October, which was only discovered and rectified recently.
The Fix
Addressing this issue isn’t straightforward. What’s needed are better tools specifically designed with cloud assets in mind. Should organizations prioritize API and credentials, shared code supply chains, insecure services, containers, and exposed databases? Perhaps all of the above.
One potential solution involves implementing a cloud-based anomaly detection system utilizing Bytewax and Redpanda for AWS cloud environments. Another option is the introduction of a new service by Red Hat Inc. called Trusted Software Supply Chain. While many security teams utilize honeynets to detect and prevent intrusions, a promising advancement involves the use of honey tokens in software supply chains.
Cloud infrastructure protection operates under a different ownership model
Cloud providers often cite that infrastructure security means understanding the division of ownership between the customer and the provider, as discussed in a post on CSOonline. However, that is a complete cop-out and one of the reasons why there are still ongoing issues with cloud security.
The challenge with a shared-ownership security model lies in the ambiguity surrounding the delineation of responsibilities, leading to vulnerabilities and incidents resulting from miscommunication and misaligned responsibilities. As highlighted in the CSA report, educating each developer on their company’s assumptions regarding shared responsibilities with the cloud provider is essential, particularly in terms of applying software patches and other mitigations following vulnerability discoveries.
For instance, the 2019 breach of Capital One’s AWS infrastructure by a malicious insider, examined in detail in a post on Diginomica by Kurt Marko, underscores this issue. While Capital One had misconfigured some firewall rules on AWS, AWS also bears responsibility due to vulnerabilities in its cloud services setup that made them susceptible to server-side request forgeries.
The Fix
The answer lies in achieving clearer delineation and resolution of the blurred lines within the shared responsibility model. The CSOonline post provides valuable suggestions on how to attain this clarity. Playbooks outlining responsibilities for patching and scanning for potential issues should clearly define roles and timing, and these roles should be rehearsed in tabletop security exercises.
Cloud identity and access management pose various challenges that demand meticulous implementation
Finally, the most challenging aspect of cloud security revolves around identity and access management, which holds the potential to impact overall security posture significantly. This concern has consistently ranked at the top of the CSA threat list, drawing continued attention from analysts.
While media attention may gravitate towards insecure cloud storage buckets, the underlying issues are more profound. For example, the implementation of multifactor authentication by organizations can play a significant role in enhancing security, provided it is effectively deployed.
Unit 42’s report found that more than half of its customers fail to enforce MFA for users with admin rights on their main web cloud consoles, which oversee their entire infrastructure. Then there is the issue of determining the appropriate MFA technology for additional factors, including hardware keys, passkeys, and biometrics. While most experts agree on the importance of avoiding certain methods, such as SMS one-time passwords, the intricacies lie in the specifics.
The transition to remote work has compounded identity management complexities, placing a heavier burden on IT departments to authenticate employees, customers, and partners.
The Fix
A proactive approach toward addressing the identity issue could involve implementing a cloud-native application protection platform.
The bottom line: there remains significant work to be done in securing an entire cloud infrastructure. And these are just five broad categories that aren’t necessarily exclusive or exhaustive. A fundamental principle remains unchanged: Any software, when used by a large number of users, is susceptible to misconfiguration by a certain percentage of those users. The existing cloud platforms have yet to address this inherent reality adequately.
To mitigate these threats, it’s advisable to enhance channels for external researchers to report potential issues directly to the enterprise’s security team.









biolean reviews
March 29, 2024Simply wish to say your article is as amazing The clearness in your post is just nice and i could assume youre an expert on this subject Well with your permission let me to grab your feed to keep updated with forthcoming post Thanks a million and please carry on the gratifying work.
zencortex reviews
April 4, 2024The breadth of knowledge compiled on this website is astounding. Every article is a well-crafted masterpiece brimming with insights. I’m grateful to have discovered such a rich educational resource. You’ve gained a lifelong fan!
yopmail
April 16, 2024Your blog is a treasure trove of valuable insights and thought-provoking commentary. Your dedication to your craft is evident in every word you write. Keep up the fantastic work!