How To Defend Against Business Email Compromise Attacks
The most common victims targeted work at organisations that weren’t using multi-factor authentication (MFA) to secure their accounts.

Business Email Compromise (BEC) attacks are one of the most lucrative forms of cyber crime: According to the FBI, the combined total lost is over $43 billion and counting, with attacks in at least 177 countries.
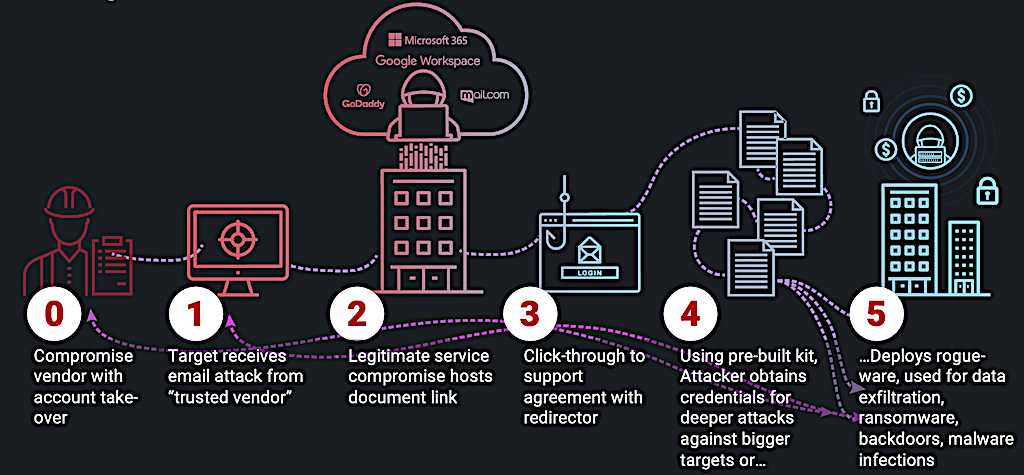
These attacks are relatively simple for cyber criminals to carry out, all they need is access to an email account and some patience as they try to trick victims into making financial transfers under false pretenses.
This commonly involves tactics such as sending messages to employees, that appear to come from a legitimate trusted source like their boss or a colleague, the attacker may suggest a payment, often very large, that must be made quickly in order to secure an important business deal.
If the victim falls for it, the entire business could be left to deal with catastrophic consequences.Fortunately, organizations can take steps to stay ahead of the curve to prevent the potential damage caused by attacks.
More advanced BEC attacks hack into a company account and use a legitimate email address to make the payment request.
It’s even been known for scammers to monitor inboxes for long periods of time, only choosing to strike when a real business transaction is about to be made, at which point they cut in and direct the payment to their own account.
With money to be made in this way, cyber criminals are increasingly turning towards BEC campaigns and businesses are falling victim.
According to cybersecurity analysts at Arctic Wolf, the number of BEC attacks to which they have responded increased drastically, and these attacks accounted for over a third of all incidents investigated.
There was a common theme among many of the victims: 80% of the organisations that fell victim to BEC attacks didn’t have MFA in place.
Multi-factor authentication provides an extra layer of security for email accounts and cloud application suites. Boosting the overall email security and cloud security.
Requiring the user to verify that it really was them who logged into the account, helping to protect against unauthorised intrusions, even if the attacker has the correct username and password.
Organisations that ignore MFA are leaving themselves open to BEC campaigns and other cyberattacks. Despite repeated recommendations from cybersecurity agencies that it should be applied.
Why Aren’t Businesses Using MFA?
MFA requires careful planning and coordination to implement successfully, ensuring that organizations can continue to operate without disruption.
Since users require cyber security awareness training in how to use the MFA system, this may be difficult for some organisations.
In addition, configuring and testing a new MFA deployment across an organisation can place a heavy burden, but it’s necessary.
Despite these potential restraints, applying MFA to all user accounts is one of the most significant things organisations can do to help protect their employees and their network from cyberattacks, so long as they’re set up correctly.
Organisations should plan their MFA deployments out well in advance to account for technical hiccups they may encounter.
In addition, organisations should take time to ensure that MFA configurations are tested ahead of prime time and that users are well-trained on how to use the new MFA platform of choice.
While MFA does help to prevent cyberattacks, it isn’t infallible and determined cyber criminals are finding ways to bypass it.
With BEC attacks using social engineering to trick people into thinking they’re doing the right thing, it’s also important for organisations to train their employees to detect when a request, even if it comes from a legitimate account, it could be suspicious.
Users should be trained to recognise suspicious financial requests. If something feels off, users should heed that instinct and inquire further. Urgent financial requests should be validated through additional means before finalising major transactions.
Phishing Awareness Training For Your End Users
It’s 2023 and Cyber Crime is still on the rise. Cyber criminals continue to relentlessly attack organizations, big and small, with more sophisticated emails, phishing, and social engineering tactics.
- 89% of phishing attacks orchestrated by professional cyber crime organizations.
- 66% of malware is now installed via malicious email attachments and advanced spear phishing techniques, costing business on average $140,000.
- 41% of IT Pros report AT LEAST DAILY phishing attacks.
- 30% of phishing emails are opened.
It’s essential that your business stay ahead of the curve, implementing a multi-layer security posture with physical controls, software controls, and end user training to prevent your easiest target from falling victim.
Here at BVA Technology Services we are partnered with Sophos to keep businesses and users safe and up to date. We highly recommend Sophos Phish Threat Service, it provides effective phishing simulations, automated training, and comprehensive reporting.
Sophos Phish Threat is a phishing attack simulation and training for your end users!
For just ($2.90/month) we’ll set you up with Sophos Phish Threat, so your organization can begin cultivating a positive security awareness culture through testing, training, and reporting.
How Phish Threat Works:
- On a reoccuring basis, Phish Threat sends out 1 of 500 realistic phishing attacks to your internal staff.
- Each email is tracked to see who opens the email, clicks on any links, and/or provides their credentials.
- Any users caught are automatically enrolled in an interactive training module that will educate the end user about the specific threat in that particular email.
- Users can report the suspected phishing email wtih the user of an outlook add-in.
- All actions are gathered in Sophos Central to provide comprehensive reporting on the users who have been caught, the number of times they have been caught, and if they have completed the training or not. This allows you to enforce accountability of those trainings.
What The Phishing User Training Covers:
- Current phishing, credential harvesting, and malicious attachment campaigns.
- Socially relevant attack simulation templates.
- Scheduled Monthly Training Campaigns.
- Covering multiple scenarios from beginner to expert.
While there’s no silver bullet when it comes to preventing all cyber security attacks, putting appropriate measures and training in place can significantly reduce the chances of it happening.








