Newly discovered cyber security threat, a cross-platform piece of malware called ‘Chaos’ is spreading on Linux and Windows systems to carry out distributed denial of service (DDoS) attacks. These attacks target online gaming firms, crypto exchanges, and rival ‘stressor’ sites renting DDoS-as-a-service. The malware, which was written in Go – Google’s popular cloud and systems programming […]
A stealthy new form of malware is targeting Linux systems in attacks that can take full control of infected devices, and use this access to install crypto-mining malware. This malware has been detailed by cybersecurity researchers at AT&T Alien Labs, they call it Shikitega. This malware targets endpoints and Internet of Things devices that run on Linux operating […]
Our mobile devices are now the keys to our communication, finances, and social lives, making them lucrative targets for cybercriminals. Whether you use a Google Android or Apple iOS smartphone, threat actors are constantly evolving their tactics to break into them. This includes everything from basic spam and malicious links sent over social media to malware […]
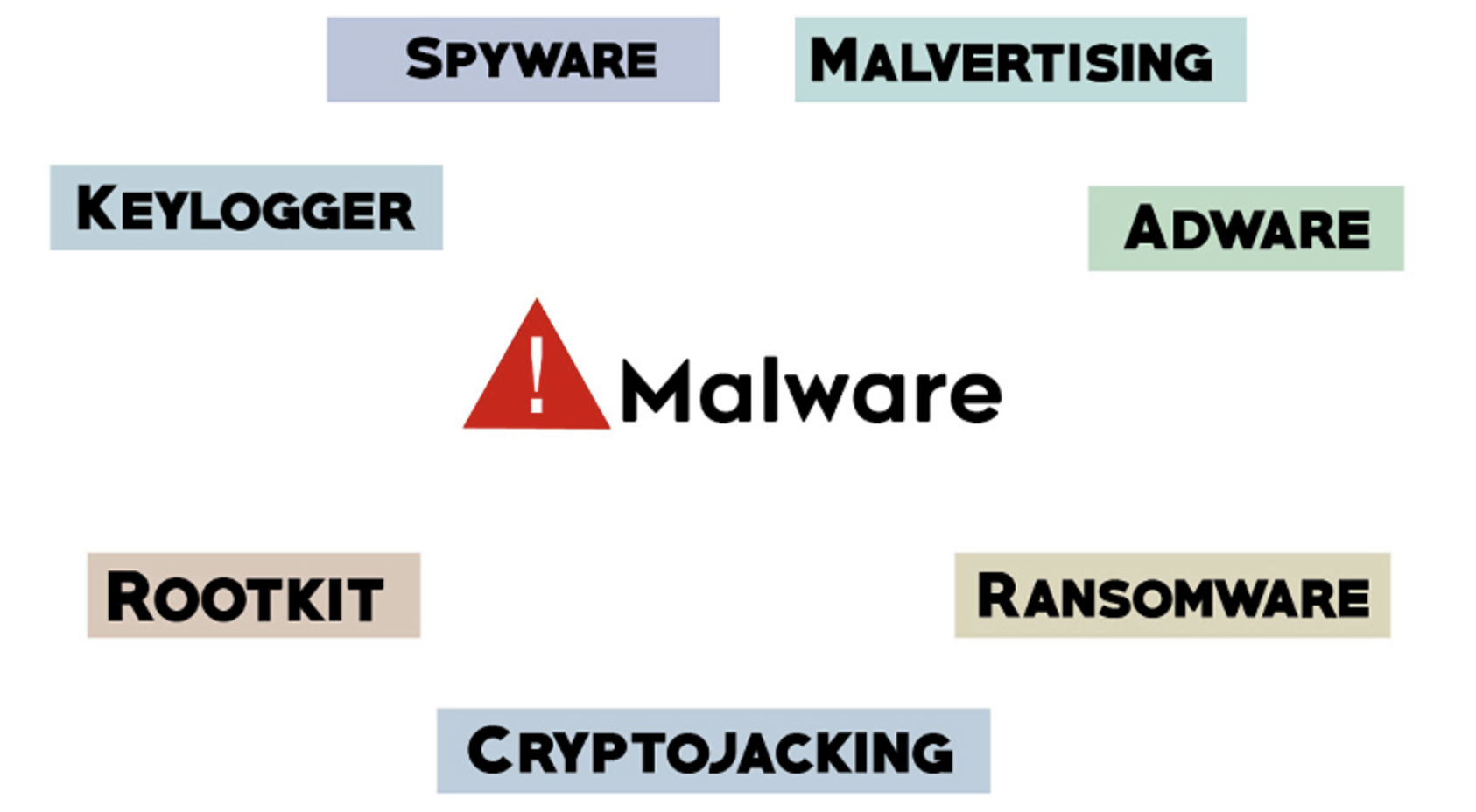
Malware Cyber Security Awareness: Managed Threat Protection Malware is a broad term for any type of malicious software designed to damage or exploit a device, service or network. Cyber criminals use malware to gain remote control over victims’ devices, spy on user activities, steal sensitive data they can leverage for financial gain, or use the […]
Increasingly, the world is going digital, and that includes how we spend. The cryptocurrency space is quickly evolving, with many new trends and products coming about. One new trend that is quickly gaining in popularity is the crypto rewards credit card. As more and more crypto cards are becoming available, consumer interest is growing to earn […]
Malware typically refers to malicious software comprised of worms, viruses, Trojans, and several other harmful programs. Hackers and spammers use Malware to damage your data and gain access to your confidential and sensitive information. While no device is immune to malicious software or infections there are effective security practices you can implement to help prevent […]