Our mobile devices are now the keys to our communication, finances, and social lives, making them lucrative targets for cybercriminals. Whether you use a Google Android or Apple iOS smartphone, threat actors are constantly evolving their tactics to break into them. This includes everything from basic spam and malicious links sent over social media to malware […]
Learn how to boost your mobile security and protect your digital identity. This tech blog will run through different forms of malicious software on your iOS or Android handset, the warning signs of a spyware infection, and how to remove such pestilence from your mobile devices if it is possible to do so. The emails […]
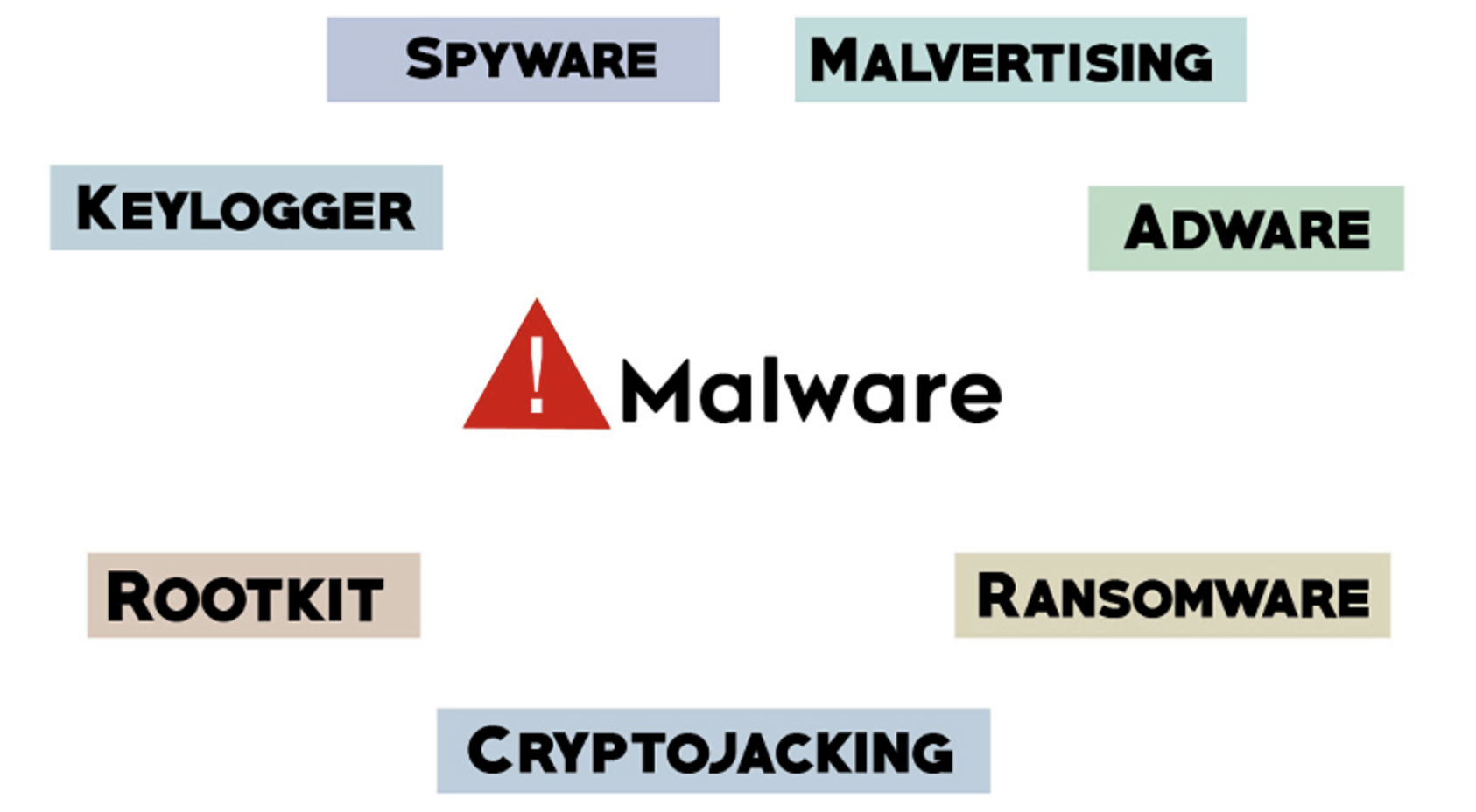
Malware Cyber Security Awareness: Managed Threat Protection Malware is a broad term for any type of malicious software designed to damage or exploit a device, service or network. Cyber criminals use malware to gain remote control over victims’ devices, spy on user activities, steal sensitive data they can leverage for financial gain, or use the […]
Malware typically refers to malicious software comprised of worms, viruses, Trojans, and several other harmful programs. Hackers and spammers use Malware to damage your data and gain access to your confidential and sensitive information. While no device is immune to malicious software or infections there are effective security practices you can implement to help prevent […]